Login.gov neutered the security of 2FA
Table of contents:
Update
This is fortunately not true, as the folks on Hacker News informed me. I misunderstood what the dialog was trying to tell me.
A personal key appears to be used only for recovering a password, not for regular 2FA login. The wording is strange because it’s not replacing a 2FA method with another 2FA method for regular authentication, but instead updating the method used for recovering a password.
I almost certainly got the personal key and threw it away, which is what I normally do.
From a UI perspective, it would be nice if it mentioned that an authentication app was already in use. Ironically, having already secured my account caused me to think that I was making it less secure.
Original post
Today, I was trying to authenticate to a government website via login.gov, which is a centralized service for logging into US government websites.
Naturally, logging into government services is a matter of utmost security. As a result, login.gov features two-factor authentication (2FA). This lets you use a second factor for logins, such as a code-generating device that you have. I had previously set up a code-generation app on my phone to increase the security of my account.
I got this message today indicating that I could no longer use this app:
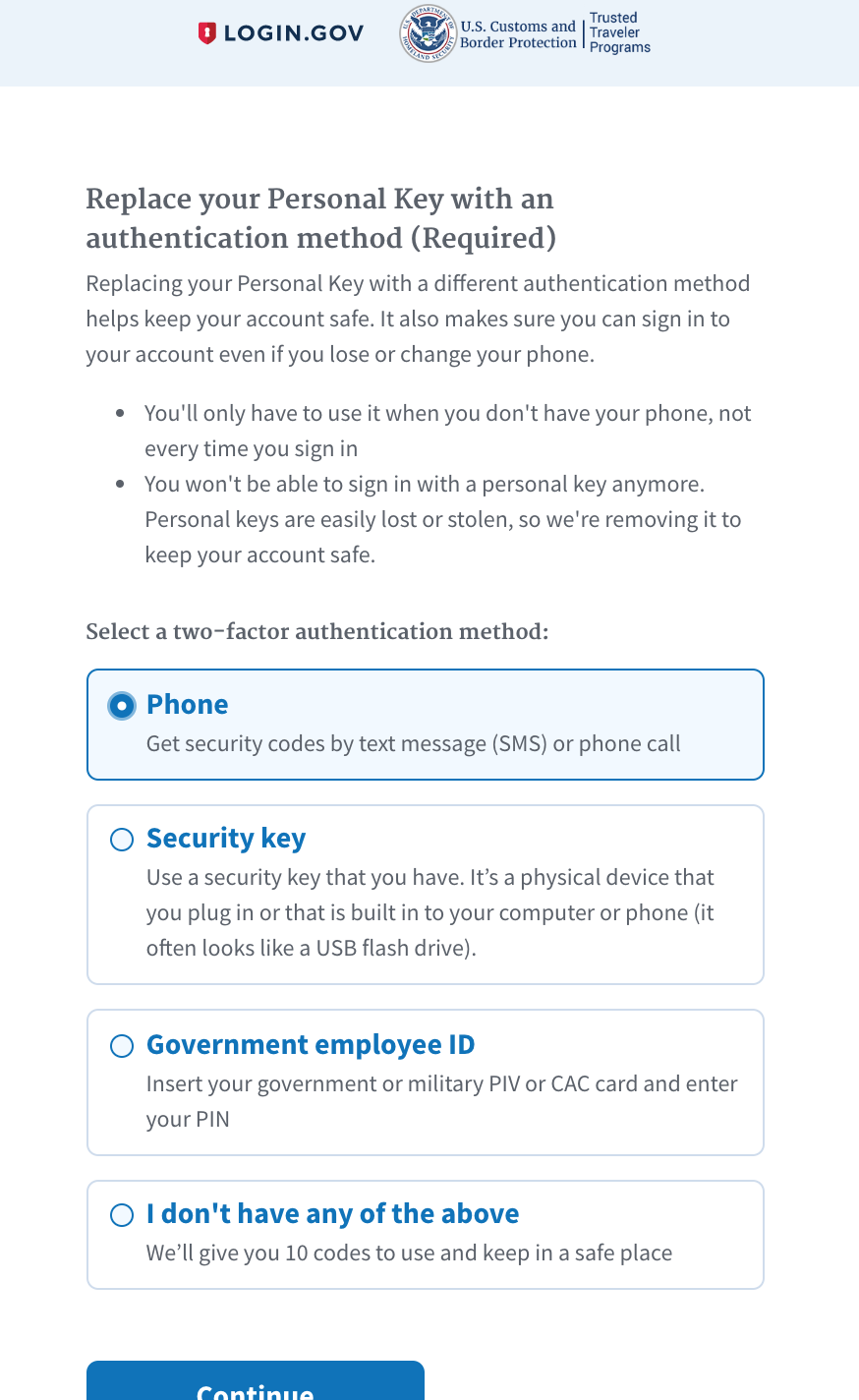
Required upgrade to a new 2FA option.
What a disappointment! I don’t have a dedicated physical security key or government security key, and I certainly don’t want to keep track of physical codes. The only option for me is SMS… which is phone-based, and the very thing they’re claiming is bad.
SMS has problems as an authentication factor. The main one is that many services let you gain access to your account using only the SMS option, which means your account really has an extra single-factor authentication method attached to it, instead of a single dual-factor authentication method.
But let’s suppose that login.gov isn’t vulnerable to this. It’s still fairly easy to hijack SMS messages via social engineering. Besides that, a dedicated attacker could also attempt to physically intercept SMS messages with special hardware.
My phone was a great authentication mechanism. To access the authentication app, you have to physically have the phone, then enter my 10-digit phone passcode (not reused anywhere else) to log in, then scan my fingerprint to access my authentication app. That’s three factors right there: something I have, something I know, and something I am. Beyond that, you also need to know my login.gov password (also not reused anywhere else).
The SMS-based approach is an unfortunate step backwards for security when it’s most important.
Related posts
The following are hand-curated posts which you might find interesting.
| Date | Title | |
|---|---|---|
| 13 Dec 2019 | (this post) | Login.gov neutered the security of 2FA |
Want to see more of my posts? Follow me on Twitter or subscribe via RSS.